Anna Kournikova Code Red Nimda This page was last edited on 14 September , at After the worm is copied to the remote host it is started there through the shell. On Windows machines, I have seen the Control Panel icons switch to the left pane, functions like FIND in the browser stop working, and many other oddities. Before proceeding further we recommend that you run a full system scan. Any unsaved changes will be lost. EXE worm aka Blaster. 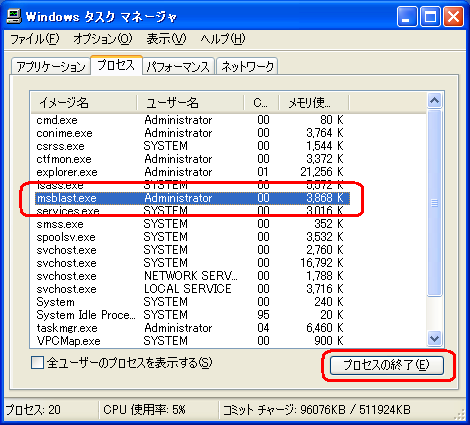
| Uploader: | Gardarr |
| Date Added: | 24 November 2004 |
| File Size: | 42.37 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 85172 |
| Price: | Free* [*Free Regsitration Required] |
By using this site, you agree to the Terms of Use and Privacy Policy. Stop making money and fix your software!! In practice this logic will start the DDoS attacks on 16th of August and will continue until the end of the year.
This results in critical memory being overwritten allowing the remote system to gain a shell on TCP port with Local System privileges. Four versions have been detected in the wild.
The compromised host will then listen on UDP port 69 for tftp connections from newly compromised systems. Submit a sample Submit a file or Exs for further analysis. For additional information about recovering from this worm, contact your antivirus software vendor.
NOTE If the file was moved to quarantineyou need to collect the file from quarantine before you can submit it. The worm also creates the following registry entry so that it is launched every time Windows starts:. Microsoft temporarily shut down the targeted site to minimize potential effects from the worm. The algorithm has a mode when it favors networks surrounding the infected host. It has a date triggered payload that launches a denial of service attack against windowsupdate.
Tell us what we can do to improve the article Submit.
| Symantec
Symptoms of Infection If your computer is infected with this worm, you may not experience any symptoms, or you may experience any of the following symptoms: Worm, will cause a denial of service on Sxe daemons.
Views Read Edit View history. Did this solve your problem?
Download the Windows patches for this vulnerability by clicking on the links below: A Trendmicroand Win After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis. This page was last edited on 14 Septemberat This dialog is coming from Windows itself, and will show the msblwst message in the localized language. First the worm fetches the IP address of the infected host and puts it into the variables above. Windows users won't see the timer.
In many cases the worm causes XP machines to start rebooting periodically with this error message:. Exclude a file from further scanning If you are certain that the file is safe and want to continue using it, ,sblast can exclude it from further scanning by the Msblzst security product.
Windows 32 bit.
Virus alert about the Blaster worm and its variants
The patch against MS fixes the MS vulnerability as well. The worm exploits a known windows vulnerability that is easily patched, however few systems seem to have this patch installed.
Bagle NetSky Sasser The worm's executable, MSBlast.
The worm also creates the msglast registry entry so that it is launched every time Windows starts: When the exploit starts on the remote machine it opens a shell through which the worm copies itself to the host using TFTP Trivial File Transfer Protocol. This will terminate the shutdown, however in most cases the system may be to unstable to try to recover and may need to be rebooted anyway. The Lovsan worm can not exploit this new vulnerability.
Summary Removal Technical Details.

Comments
Post a Comment